
How can you be sure that patient information you share electronically with other physicians is not as accessible as a note on a postcard?
Fam Pract Manag. 2000;7(9):37-40
Do security concerns prevent you from using e-mail for clinical correspondence? When you send an e-mail message, are you worried that the contents might pass by an unintended reader's eyes?
Unless you're using what's known as encryption technology, you cannot transmit confidential e-mail messages safely. Without it, those with a desire can intercept and read your messages, create messages in your name or change your messages. With the protection of an encryption system, e-mail is a secure form of communication.
The security of one encryption system, Pretty Good Privacy (PGP), brought praise from the National Security Agency's Deputy Director, William P. Crowell, who in 1997 said, “If all the personal computers in the world — 260 million — were put to work on a single PGP-encrypted message, it would still take an estimated 12 million times the age of the universe, on average, to break a single message.”
Today, such powerful encryption software is available free of charge, and, if you are at all comfortable with your computer, it's easy to use. If you and the physicians with whom you consult adopt compatible encryption programs, you can easily make the Internet a secure communications medium.
KEY POINTS:
Without encryption, e-mail is not a secure form of communication.
Inexpensive, even free encryption software can help guarantee the privacy of your e-mail messages to other physicians.
Public-key encryption makes it easier to maintain the security of the key used for decrypting messages.
E-mail is like a postcard
Unlike paper messages, which move physically from one place to another when they are sent and typically exist in only one place at a time, electronic messages are routinely duplicated when they are sent from one computer to another across the Internet.
Why is this significant? When a letter is delivered in an unopened envelope, the recipient can generally assume that there are no copies of the letter in the post office or the mail room or anywhere else. When an e-mail message is delivered, odds are that numerous copies of the message have been created along the electronic trail back to the originator, and neither the sender nor the recipient know where those copies are or who has access to them. Normally, each computer simply forwards all messages not specifically addressed to it. But someone wishing to intercept messages can do so just by reprogramming one of these computers that messages pass through to give him or her access to messages it forwards. [See “How Safe Are Computerized Patient Records?” FPM, May 1997, page 34.]
Unless you can control access to it, e-mail is the electronic equivalent of a postcard. Just as you wouldn't think of putting confidential information on the back of a postcard, you ought to have the same hesitation when composing unencrypted e-mail messages.
Security through encryption
Encryption is like an electronic combination lock: The sender encodes the text of a message, causing it to appear as a series of seemingly random characters and symbols. A recipient can only decode it with the right key (see “What encryption looks like.”)
What encryption looks like
When you receive an encrypted e-mail, the text will be unreadable. It may look something like this.
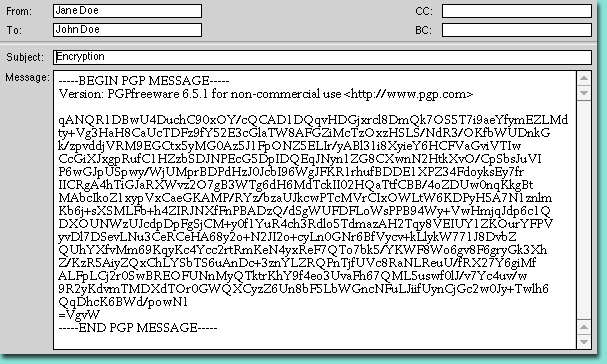
Eliminating risk through such means may seem like overkill, but the security concerns brought on by the onslaught of e-mail and other far-reaching technologies are undeniable. Technology can provide the necessary security —through encryption. Two encryption systems are currently in common use — the traditional secret key and the public/private key methods.
Secret keys. Also known as symmetric, conventional or single-key systems, these require the sender and recipient to use the same key for encryption and decryption. The problem is safely sharing the key. Sharing your key via e-mail defeats the purpose of using encryption. You could send the key through traditional snail mail, but that takes time. If you're trying to request a consult, for instance, you might as well just mail the consultant a letter.
If you expect to correspond repeatedly with the same person, go ahead and opt to send your key via traditional mail. You will be able to exchange encrypted e-mail after that for as long as you desire.
More than two people can share a single key, which can work well in private networks. However, for those who want to share messages beyond their internal network, a public key may be more appropriate.
Public/private keys. With public key (or asymmetric key) systems you own a pair of separate, but related, keys — a public key that anyone can use to encode the messages they send you and a private key that you use to decode those messages.
The public key can be widely shared, by posting it on a Web site, for example, since it cannot be used to decode messages. The private key, on the other hand, needs to be kept secret. To prevent other people who might have access to your computer from using your private key to decrypt and read confidential messages you've received, your private key (which is encrypted) should be kept on your hard drive and only retrievable through a password.
When shopping for encryption software, be sure to use a package with built-in key generation capabilities. Another area to look out for is key size. Keys are comprised of bits, and the bigger the public key, the more secure the system. (A public/private key of 1,000 to 2,000 bits is sufficient.) The size of secret keys and public/private keys should not be directly compared because a public/private key is about 20 times larger than a corresponding secret key. You might wonder why a public/private key is so much larger than, for example, a 128-bit secret key found in most domestic browsers. It's because the algorithms are totally different, so it's like comparing apples and oranges (see “Sources for encryption software”).
Sources for encryption software
While this is not intended to be a complete list of sources, it does give a sense of what is available for use by individuals. Note that at least one program, PGP Freeware, is available without charge. Others have more features (e.g., file encryption to protect data stored on your computer disk) and may integrate more seamlessly with your e-mail program. You can learn more about the various programs from the Web sites listed below.
Aliroo
PrivaSuite
www.aliroo.com
713-723-6000
Starts at $99 per user
Celo Communications
CeloCom Mail
www.celocom.com/web/celo/d.asp
650-938-7600
Starts at $49 per user
Entegrity Solutions
Entegrity AssureMail
www.entegrity.com
408-487-8600
Starts at $100 per user
Massachusetts Institute of Technology
PGP Freeware
http://web.mit.edu/network/pgp.html
Free to individual users
McAfee.com
PGP Personal Privacy
www.mcafee.com/products/
800-338-8754
Starts at $19.95 per
Encryption: Step-by-step
If you would like to try your hand at encryption, here's how to download a free version of PGP (the encryption system I use), send me an encrypted message and receive one in return.
The instructions may seem cumbersome, but the process is really quite simple once you've gone through it a few times. The first four steps, which download the software and establish your keys, need to be completed only once. Similarly, steps 5 and 6 are done only once for each correspondent. After that, sending and receiving messages are simple two-step processes.
Installation can take from one to two hours, depending on whether you already have the necessary software on your computer, how comfortable you are with computer installations and the speed of your computer and Internet connection. Keep in mind that the download process may vary slightly from computer system to computer system. Before you begin, be sure to close all applications and extensions and turn off your virus protection. Because the program is large, you will also need to have some type of file expander program, such as Aladdin Expander (www.aladdinsys.com/expander), downloaded on your computer.
Obtain PGP
1. Download PGP. The Massachusetts Institute of Technology has a Web page where you can obtain PGP for free: http://web.mit.edu/network/pgp.html. Go to that page and select the version of PGP that suits your operating system. Follow the prompts, which will include accepting the license agreement and will ultimately bring you to installation. Save the PGP Free-ware folder to your desktop.
2. Install PGP on your computer. Open the installer. Follow the prompts. When the installation is complete, restart your computer and renew your Internet connection. You should also restore your extensions and virus protection.
3. Create your own key pair. Go to the PGP folder that was created as part of the installation process (not the PGP Freeware folder you saved to your desktop in Step 1) and double-click the PGP Keys icon to create your own key pair. Follow the prompts, one of which will ask you to supply a password that guards your private key. Once you've created this password, which you should not forget, your key pair will be generated.
4. Send your public key to the PGP server. With your Internet program already launched, you will be prompted to click the box to “Send key to root server,” which is the PGP server. Putting your public key on the PGP server allows others to locate it when sending you encrypted mail.
Send me an encrypted message
5. Find the public key of the person you want to send a message to. My public key is readily available at my Web site (home.pacbell.net/dbhill/PGPKey.html) or it can be queried from the PGP key server at pgpkeys.mit.edu:11371. If you were to search for my name at the key server, you would get several lines of cyphertext, surrounded by banners announcing “BEGIN and END PGP PUBLIC KEY BLOCK.”
6. Import your correspondent's key. Copy the entire block, including banners, and paste it to a temporary file in your word-processing software program. Save the file as a text-only file. (It doesn't matter where you save the file, and you can safely trash it after you complete step 6.) Then open the PGP Keys icon in your PGP folder. Finally, under “Keys” on the toolbar, select “Import” to bring the key into your PGP Keys tool. You will see my name, plus some technical information about the keys.
7. Compose an e-mail message. Go ahead. Write me a message.
8. Encrypt the message. Copy the block of text in the e-mail you want encrypted. Open PGP Tools in your PGP folder. Select the “Encrypt” icon from the PGP menu. Click “Clipboard.” You will be prompted to choose which public key(s) you want to use. Select my name from the “User” list and drag it to the “Recipient” list. Click “OK.” Go back to your e-mail and use the “Paste” function to pour what is now encrypted copy back into your e-mail, making sure you delete the unencrypted text that you copied earlier, and send your e-mail. When I receive your encrypted message, I will be able to decrypt it using my private key.
Receive and decrypt a message from me
9. Watch for incoming mail from me. Once I've received and decrypted your message, I'll look up your public key and send you an encrypted reply.
10. Decrypt my reply. After opening my e-mail, copy the encrypted text, including “——-BEGIN PGP MESSAGE——-” and “——-END PGP MESSAGE——-.” Open the PGP Tools icon in your PGP folder. Select the “Decrypt/Verify” icon from the PGP menu. Click “Clipboard.” You will be prompted to supply your private key password. Copy the decrypted text to a word-processing file, and voilà, you will be able to read my reply. To send mail to another person, begin with step 5.
Wrapping it up
While the steps I've described may seem cumbersome, once you try encryption a few times you will get the hang of it and rely on it for secure communication. After all, the electronic communication we use can be a great help in the day-to-day management of our practices, but it comes with a cost.
While it expedites communication, it also facilitates eavesdropping on that communication. If your software doesn't allow you to protect your patient's confidentiality, then it is a hindrance to your practice, not a help. By encrypting confidential information, you are doing your part to protect your patient's privacy.